MSSPs Get Zero Trust Ready for Customers Who Need Your Help
by Simon Moran
Posted on September 21, 2021
Want to interview Simon?
Contact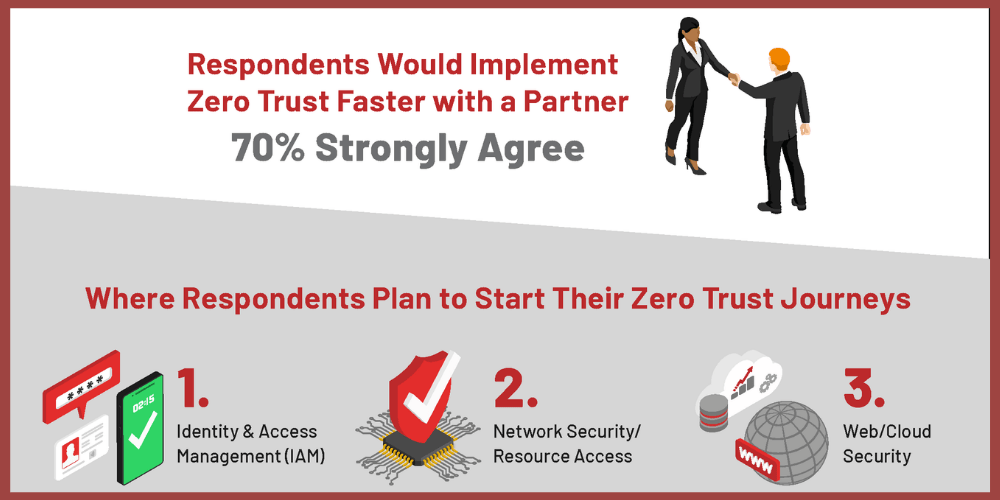
A new survey of nearly 1300 security and risk professionals, conducted by Ericom Chief Strategy Officer Dr. Chase Cunningham, highlights the need for MSSPs in the new Zero Trust world. As shown in the report published last week, over 80% of those surveyed see Zero Trust as a necessary strategy; 70% believe that they could implement Zero Trust faster if they had a partner who could help. Zero Trust is a new frontier and service providers can play a valuable and important role as knowledgeable guides and advisors for organizations who are entering territory that is uncharted for them and in fact, fairly new for the market as a whole.
With 96% of security pros believing that Zero Trust security stops or limits the success of attacks, service providers who continue to offer only legacy managed services such as VPNs, on-premises firewalls and endpoint protection are doing a disservice to their customers. By failing to educate even customers who specifically request these services regarding their vulnerability and the availability of more secure options, they are increasing the likelihood that the organizations they serve will be successfully breached.
Beyond their duty to protect customers and advise them, managed service providers who continue to focus on perimeter-based protection will be missing out on a rare revenue opportunity. By developing Zero Trust security expertise – and establishing their bona fides – just as demand is beginning to build, forward-looking MSSPs will benefit from the surge of planned transitions to Zero Trust approaches and the built-in stickiness of customers that opt for managed Zero Trust secure access service edge (SASE), secure web gateway (SWG), remote browser isolation (RBI), identity and access management (IAM) and zero trust network access (ZTNA) solutions.
The survey shows that this transition is happening now. Over 80% of organizations plan on moving to enable Zero Trust in the next year and half of those are planning to start their move within the next quarter. But that does not mean that they think the change will be fast or easy: They are well aware that true, end-to-end Zero Trust security can be difficult to achieve and maintain. After all, there are so many pieces and so much management required.
With over 28% of respondents citing budget restrictions as the reason Zero Trust implementation might be delayed and another 20% concerned about conflicts with other IT/business frameworks, service providers should aim to offer Zero Trust solutions that:
- Are built and priced for midsized organizations, which may not have deep enough pockets to implement end-to-end Zero Trust in one go.
- Support as many modular Zero Trust apps as possible into one platform, so that functionality can be added gradually.
- Interoperate with other IT and business frameworks to maximize security and enable integration during gradual transitions to Zero Trust.
- Include Identity and Access Management (IAM), which almost half the security and risk professionals surveyed believe is important for overcoming roadblocks to Zero Trust security implementation and enhancing security.
Of course, MSSPs must ascertain that the solutions they offer their customers meet their own business needs as well. This means seeking a Zero Trust security platform that:
- Is built and priced for service providers.
- Integrates as many Zero Trust apps as possible into one platform, since a single platform can be more quickly deployed and more easily managed by fewer personnel.
Together, these factors add up to gross margins that enable MSSPs to achieve their goals.
Until recently, almost all Zero Trust vendors targeted their solutions toward large enterprises and priced them accordingly. To make Zero Trust security accessible to the rest of the world three things are needed:
- A Managed Services wrapper to bridge the skills gap of smaller organizations.
- Pricing that is half the benchmark set by vendors that create large enterprise solutions.
- Technology that utilizes machine learning and artificial intelligence (ML/AI) to tame the task of provisioning user policies down to each individual user, so that true Zero Trust can be achieved.
Making Zero Trust easy isn’t easy. It takes revolutionary technology, reimagining managed services, and a new approach to the underserved midsize enterprise and small business market. Have a look at the eye-opening survey by Dr. Zero Trust, Chase Cunningham by downloading it now. And check out our Zero Trust platform that is built specifically for MSSPs, by a team that has been partnering with service providers for decades.
About Simon Moran
Simon manages Ericom global business development and technology partnerships. Previously, as VP Cloud Security at Symantec Corporation, he focused on enabling next gen solutions for Cloud Infrastructure deployment. Along with a unique balance of sales, management and technical skills, Simon has over 34 years of software experience at the world’s largest and most successful software companies including Blue Coat, Oracle, SAP, and Software AG, and over a quarter century of experience in Enterprise Application sales of Security, Customer Experience and Supply Chain software.Recent Posts

Air Gapping Your Way to Cyber Safety
Physically air gapping enterprise networks from the web is a great way to protect operations, keep data safe … and squelch productivity. Virtual air gapping is a better approach.

Motion Picture Association Updates Cybersecurity Best Practices
The MPA recently revised its content security best practices to address, among other challenges, the issue of data protection in the cloud computing age.

FTC Issues Cybersecurity Warning for QR Codes
QR codes on ads are a simple way to grab potential customers before they move on. No wonder cybercriminals are using QR codes, too.