HTML Smuggling Evades Traditional Cybersecurity Solutions
by Nick Kael
Posted on November 17, 2021

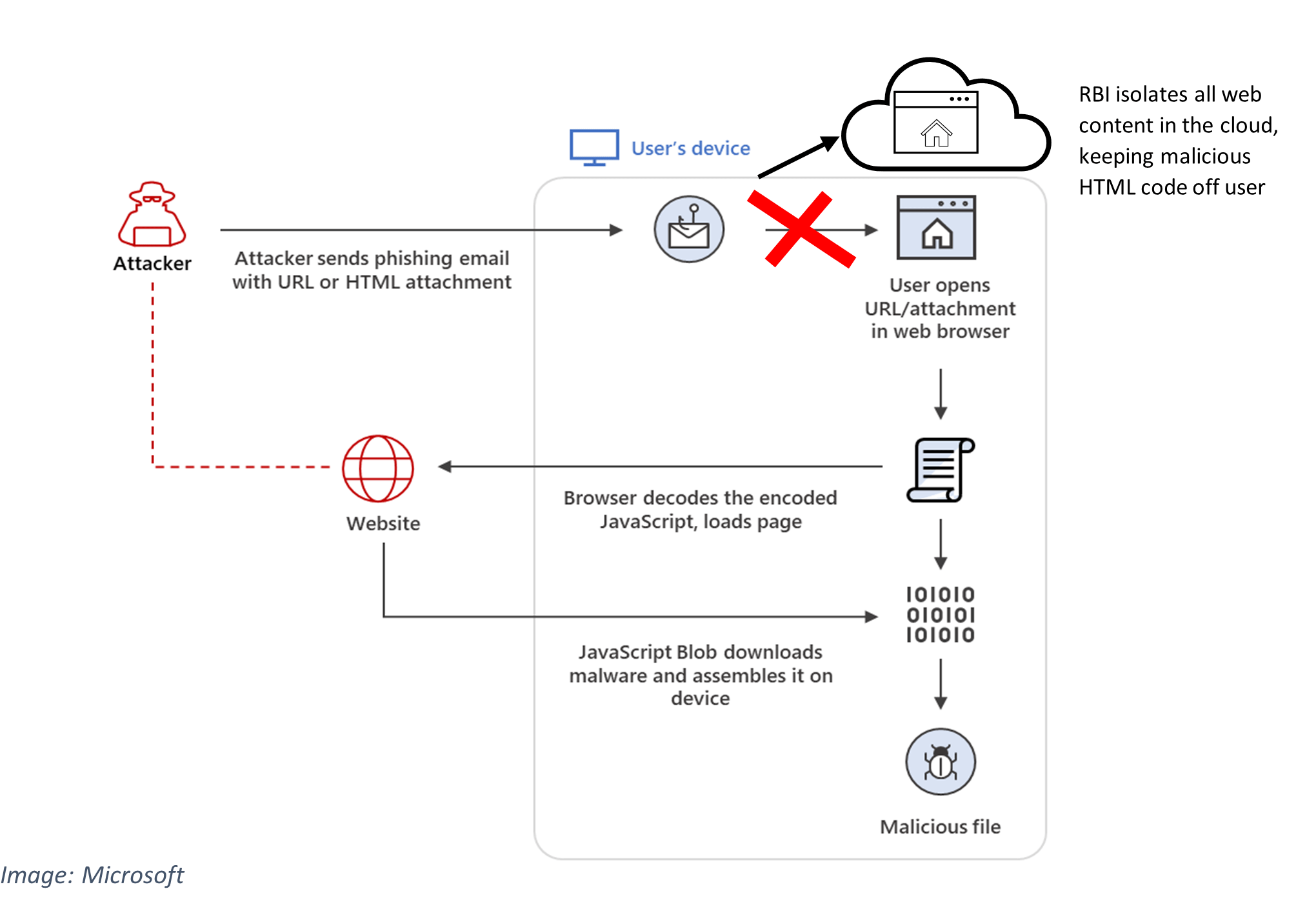
Microsoft’s 365 Defender Threat Intelligence Team recently issued a warning about a worrying increase in HTML smuggling attacks, in which hackers “smuggle” encoded malicious script via emails, using either a specially created HTML attachment or a link to an HTML smuggling page.
HTML smuggling takes advantage of HTML5 and JavaScript features supported by all standard browsers. When a user clicks a link, the “download” attribute that is used for anchor tags is leveraged to automatically download the file referenced in the “href” tag and saved to the user’s device.
JavaScript Blobs, which are also downloaded when the link is clicked, store a file’s encoded data which is decoded by the JavaScript API. In ordinary circumstances, the API would “expect” a URL that would have to be manually clicked to download. In HTML smuggling, since the Blob contains data of the file, the user doesn’t need to click anything to download the malware; just opening the page will execute the JavaScript and begin the download of the malware.
These types of attacks can foil most traditional cyber defenses. To anti-malware defenses, the code appears to be normal HTML and Javascript, so it’s not generally identified as a threat. There is no malicious executable file for anti-malware software to detect: the script assembles the payload on the host device, building the malware locally behind the firewall.
HTML Smuggling and Spear Phishing
Nobelium, the cybergang that was responsible for the Solar Winds supply chain attack, launched an HTML smuggling campaign in January 2021. The campaign, which is ongoing, has evolved, indicating that Nobelium has been experimenting with different ways to foil cyber defenses.
Starting in May 2021, Nobelium used Constant Contact, one of the most popular mass emailing services, to distribute malicious URLS. The cybercriminals masqueraded as a development organization. This campaign is known to have targeted at least 3,000 accounts in 150 different organizations. The attacks were tailor-made for each organization, designed to allow the attack to remain undetected for as long as possible within a particular organization.
Protecting Against HTML Smuggling
As for phishing campaigns, organizations rely on educated users to serve as the first line of defense against HTML smuggling attacks. As the argument goes, if users do not click on links or open an HTML attachment of emails that might be suspicious, the attack will be foiled before it begins.
However, as we’ve reported, 65% of organizations that were hit with a phishing attack had previously conducted anti-phishing training. Effective training can reduce the number of users who click on suspicious emails, although the reduction is rarely to zero. For the most well-crafted social engineering appeals, the percentage of clickers is significantly higher. And for an HTML smuggling attack, even one click can result in ransomware being deployed across a network.
It’s possible to use behavioral rules to identify and thwart HTML smuggling by, for instance, checking for ZIP files or password-protected attachments. Likewise, admins can block JavaScript from launching downloadable executable content on endpoints. However, these protections are likely to interfere with legitimate email uses as well.
A far more reliable way to foil HTML smuggling attacks even if a user clicks the link or opens the attachment is with Remote Browser Isolation (RBI).
RBI renders website content in a remote container in the cloud. No code, including HTML instructions or JavaScript, runs directly on the user’s device – or even reaches it. Instead, it is run in a virtual browser within a container isolated in the cloud. Users interact on their devices with safe rending data, using their regular browsers, while endpoints and networks remain protected from web-borne threats.
RBI is just one element of a comprehensive Zero Trust approach to network security. Web Isolation is built into ZTEdge, Ericom’s comprehensive Zero Trust Secure Access Service Edge (SASE) platform for midsize enterprises. ZTEdge provides protection against many other kinds of threats as well, while simplifying secure, from-anywhere no-VPN access to the resources users need. Capabilities including microsegmentation and identity and access management (IAM) help minimize damage in the event that a breach does occur.
About Nick Kael
A cybersecurity expert with over 20 years of experience in web technologies, architecture, infrastructure, networking and dev environments, Nick is responsible for solution management, technology strategy and technology partnerships. Nick was previously Symantec Group CTO for Global Service Providers, following his tenure as Director of the Chief Architect Team for Channel and Service Providers at Zscaler and an earlier position in the Symantec CTO organization. His certifications include CEH7, CCSK, BCCPP, Bluecoat Blue Knight, MCSE + Security, CCDP, CCNA, CCSA, VTP5 and VTSP5.Recent Posts

Air Gapping Your Way to Cyber Safety
Physically air gapping enterprise networks from the web is a great way to protect operations, keep data safe … and squelch productivity. Virtual air gapping is a better approach.

Motion Picture Association Updates Cybersecurity Best Practices
The MPA recently revised its content security best practices to address, among other challenges, the issue of data protection in the cloud computing age.

FTC Issues Cybersecurity Warning for QR Codes
QR codes on ads are a simple way to grab potential customers before they move on. No wonder cybercriminals are using QR codes, too.