Lessons Learned from Ireland’s Healthcare System Ransomware Attack
by Nick Kael
Posted on January 26, 2022
Want to interview Nick?
Contact
In May 2021 Ireland’s public healthcare system, the Health Services Executive (HSE), was hit with a ransomware attack that proved to be extremely costly and disrupted healthcare for months.
A detailed post-mortem of the attack, produced by consulting firm PriceWaterhouseCoopers, (PWC) runs to 150 pages. The report includes not only a description of what happened, but an analysis of mitigating factors and recommendations as well. There’s a lot that can be learned from this attack and from the PriceWaterhouseCoopers report.
HSE Ransomware Attack Impact
HSE provides all of Ireland’s public health services. It’s the country’s largest employer, with more than 130,000 employees working at over 4,000 locations, including 54 hospitals, on over 70,000 end-user devices.
On May 14, 2021, an attacker executed Conti ransomware on HSE systems. The organization immediately implemented its Critical Incident Process, switching off all IT systems and disconnecting the National Healthcare Network from the internet.
Those actions cut off the attacker’s access to the HSE system – but at a tremendous price to the health system and the public that depends on it. All healthcare staff immediately lost access to all IT systems, including patient records, clinical care systems, and laboratory systems. Non-healthcare activities, such as payroll and procurement, also went offline. Staff reverted to pen and paper.
- Email and networked phone lines were lost. Workers had to use cell phones, analog phone lines, and fax.
- Healthcare services were severely disrupted across the country, impacting thousands of patients.
- It took over four months for HSE to fully recover from the attack.
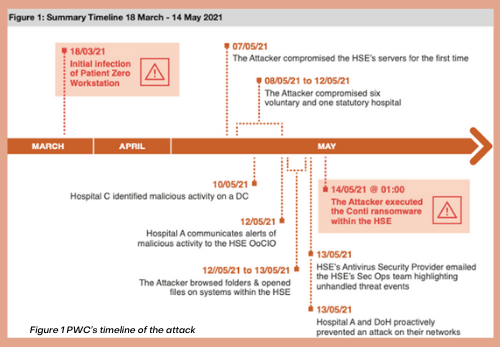
Timeline and Methodology of the HSE Ransomware Attack
While May 14 was when the Conti ransomware was deployed, the HSE network was actually infected on March 18, 2021, nearly two months earlier, when a staff member opened a malicious Microsoft Excel spreadsheet that was attached to a phishing email received two days before.
Within days, the attacker achieved persistence on the user’s workstation, ensuring continued access to the HSE environment even after a restart. HSE antivirus software detected Coblt Strike and Mimikatz on the staff member’s workstation a number of days later but did not block malicious commands since it was set to “monitor” mode.
Starting early in May – almost two full months after the initial infection — the attacker exploited their unauthorized access to compromise several servers, exfiltrate data, and move laterally to HSE hospital servers. HSE IT staff spotted activity on two hospitals’ servers but concluded that risk was low since the threat was remediated by their antivirus software. Neither ended up launching an official incident. An attempt to compromise Department of Health networks was detected and blocked, successfully protecting DoH infrastructure from attack.
On May 14, the attacker executed the Conti ransomware at 1 AM. Less than two hours later, hospitals began reporting to HSE IT staff that their systems that were locked by ransomware, and some hours later HSE shut down all IT systems and network access.
Restoring half of the servers and applications took a month. All servers were not decrypted until September 21, four months after the ransomware was deployed.
Mitigating Factors
As damaging as this attack was, it was relatively unsophisticated, relying on standard software and techniques. PWC cites this as a mitigating factor: if the attacker had been more sophisticated, the damage could have been much greater. The report cites several ways in which the attack could have been worse, including:
- If medical devices had been targeted
- If the software had acted to destroy data at scale
- If the software had auto-propagation capabilities
- If cloud systems had also been encrypted
Another mitigating factor is that the attacker actually released a decryption key on the 20th of May. Note that even with a decryption key it took months to get everything back online.
What Went Wrong
Numerous shortcomings and gaps in HSE’s technical and organizational preparedness, response, and recovery processes contributed to the success of the attack. But a few key things might have prevented it or significantly minimized its impact:
- HSE had insufficient endpoint protection capabilities, including email threat mitigation to protect against phishing attacks and solutions to disarm malicious files before downloading them to endpoints.
- There were several opportunities to stop the attacker before the ransomware was launched; even though abnormal activity was detected, proper investigations were not initiated. If prompt action had been taken, the attack could have been stopped before the ransomware was launched.
- The report recommended improving security awareness in general and phishing awareness in particular. However, relying on user training alone to achieve zero clicks on phishing emails is clearly insufficient: In an organization with 130,000 employees, even a tiny 0.1% failure rate would result in 13 clicks for a phishing email sent to just 10% of users.
The report points to underinvestment in cybersecurity as a prime reason the attack succeeded. It states,
The HSE is operating on a frail IT estate that has lacked the investment over many years required to maintain a secure, resilient, modern IT infrastructure. It does not possess the required cybersecurity capabilities to protect the operation of the health services and the data they process, from the cyberattacks that all organisations face today.
This is a lesson that every enterprise should attend to. Cybersecurity is not free, but the cost of implementing a state-of-the-art cybersecurity defense is small compared with the cost of having operations completely shut down for days or weeks.
How to Avoid Becoming a Victim
The PWC report contains several recommendations that are specific to HSE, including organizational changes, updates to infrastructure, and continuity and crisis management planning, as well as tactical recommendations.
Despite the damage that was done, this was not a highly sophisticated attack. Any comprehensive Zero Trust security approach, such as ZTEdge, might have stopped the attack entirely, and certainly would have minimized damage if the attack did slip past defenses.
These are just a number of ways that Zero Trust-oriented techniques could have stopped or mitigated this attack:
- Remote Browser Isolation (RBI) with Content Disarm and Reconstruction (CDR) can prevent malware infections by isolating malicious code in the cloud, so it can’t run on – or even reach – user endpoints, networks or servers. This would effectively have prevented the Conti malware from being installed on the infected device.
- An Intrusion Prevention System (IPS) would have detected and stopped the suspicious activity that was happening prior to the execution of the ransomware.
- Microsegmentation and Least Privilege Access could have minimized damage by limiting lateral movement within the network.
Conclusion
Even relatively unsophisticated attacks can wreak havoc on an organization that is insufficiently prepared.
Attacks such as the one on Ireland’s Health Services Executive demonstrate just how high the stakes are. And with the number of cyberattacks per day steadily growing, the risk is broad as well as high.
Patchwork approaches to cybersecurity are no longer enough. To stay safe in today’s environment requires moving away from old perimeter and detection-based methodologies to comprehensive state-of-the-art Zero Trust cybersecurity: a cloud-based Secure Access Service Edge that can effectively reduce cyber risk for distributed organizations.
About Nick Kael
A cybersecurity expert with over 20 years of experience in web technologies, architecture, infrastructure, networking and dev environments, Nick is responsible for solution management, technology strategy and technology partnerships. Nick was previously Symantec Group CTO for Global Service Providers, following his tenure as Director of the Chief Architect Team for Channel and Service Providers at Zscaler and an earlier position in the Symantec CTO organization. His certifications include CEH7, CCSK, BCCPP, Bluecoat Blue Knight, MCSE + Security, CCDP, CCNA, CCSA, VTP5 and VTSP5.Recent Posts

Air Gapping Your Way to Cyber Safety
Physically air gapping enterprise networks from the web is a great way to protect operations, keep data safe … and squelch productivity. Virtual air gapping is a better approach.

Motion Picture Association Updates Cybersecurity Best Practices
The MPA recently revised its content security best practices to address, among other challenges, the issue of data protection in the cloud computing age.

FTC Issues Cybersecurity Warning for QR Codes
QR codes on ads are a simple way to grab potential customers before they move on. No wonder cybercriminals are using QR codes, too.