What is a cloud access security broker (CASB)?
What do cloud access security brokers do, and what services do they offer?

An increasing number of organizations, large and small, are choosing to store their corporate data using cloud services. Some of this data may have valuable or sensitive content, and there could be harsh consequences if it was lost or stolen. In addition, many organizations use applications that are accessed via the cloud. Thanks to this increased cloud presence in the corporate digital landscape, a cloud security solution, such as CASB, is now of paramount importance.
As an example, many organizations choose to use Office 365, a popular MIcrosoft Software as a Service (SaaS) product that is based in the cloud. Office 365 allows its users to store and share documents through the cloud. When an application like this is in use, the implementation of appropriate cloud security solutions is crucial. CASB isn’t suitable just for SaaS environments, but also supports PaaS (Platform as a Service), and IaaS (Infrastructure as a Service) usage, making it a flexible and comprehensive enterprise security solution. Many CASB solutions can also be integrated with various authentication applications, such as Azure Active Directory (AAD), which provides secure single sign-on capabilities to its users.
How does CASB work?
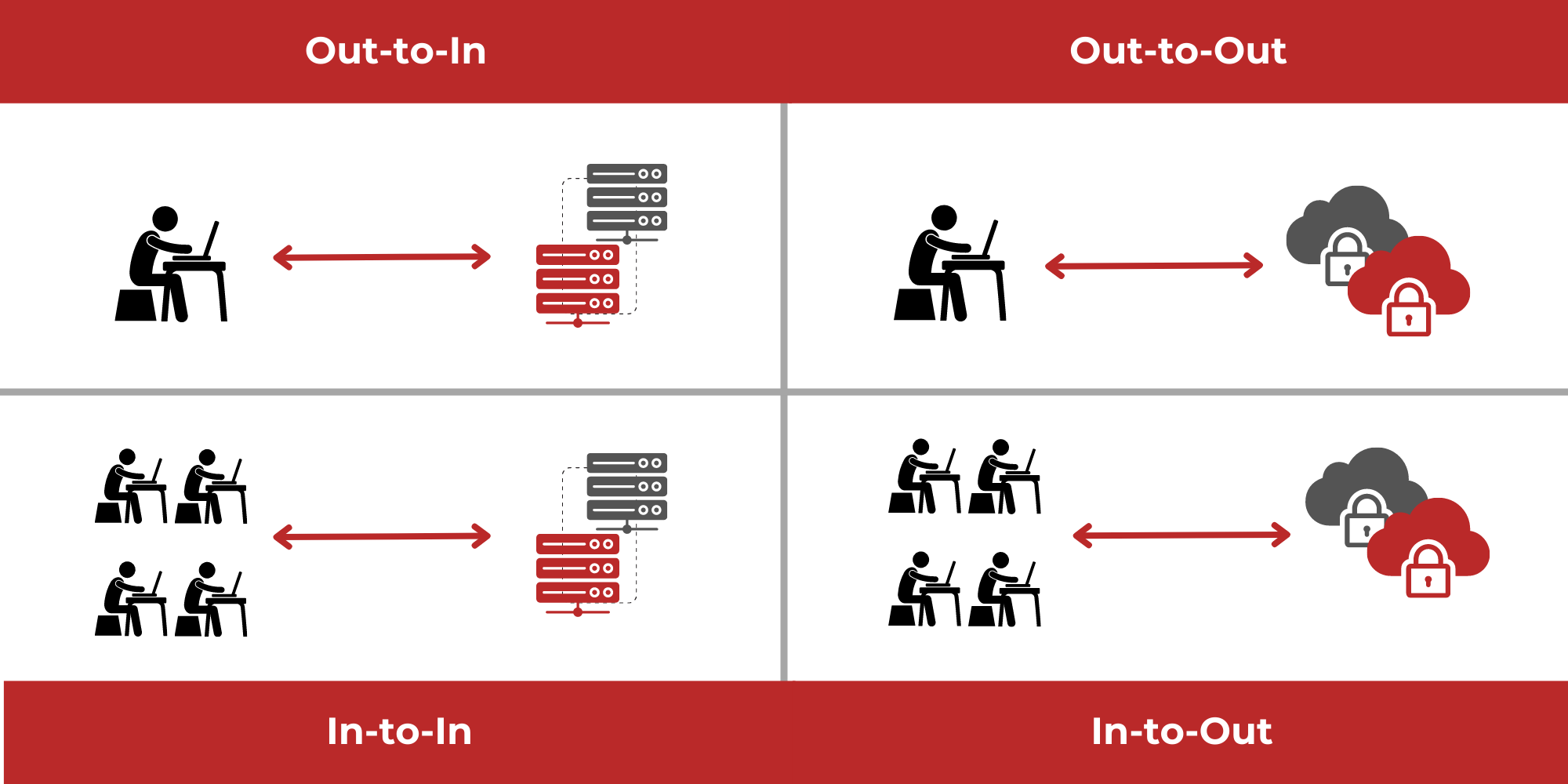
CASB is most accurately described as a combination of a filter, firewall, and proxy, which provides a protective layer between end-users and the cloud. It allows management of all of an organization’s network security policies to be fully aligned, so that the same security policies can be applied both locally (on premises), and to applications and data stored in the cloud.
CASB uses a ‘discovery-analysis-remediation’ cycle to identify potential sources of risk and respond to them effectively. First, the CASB solution discovers all cloud services in use, and gathers information about them. Then, it analyzes and classifies each cloud service according to its estimated risk level. Finally, granular policies are applied and enforced, taking into account the calculated risk level of each service to ensure security and determine the most effective course of action when a security policy is violated.
Learn How to Better Secure Access to SaaS Applications
The four pillars of CASB
According to Gartner, critical cloud access security broker use cases can be split into four main categories. These are referred to as ‘the four pillars of CASB’. The four pillars are visibility, compliance, data security, and threat protection.
Visibility
The first pillar of CASB is visibility. Even when an organization uses multiple different cloud services and environments, all cloud app usage must remain completely visible, even when no longer under the ‘jurisdiction’ of organizational network policies. CASB solutions provide visibility and control in such situations. The CASB can show which devices and users are leveraging cloud applications, and from which location they are accessing them. This granular level visibility allows for better network access control, so that detailed cloud security policies can be created for secure access to cloud apps or data. For example, access could be granted or blocked based on the user’s location and device, and whether it fits in with expected usage patterns. This is in contrast to other enterprise security solutions, which provide limited functionality for logging cloud usage.
CASB will also allow detailed risk assessments for cloud applications, alerting security professionals to any vulnerabilities that may require action. If a particular cloud app is flagged as high risk, it may be a wise decision to block the app, so that it can no longer present a risk to the organization, at least while a solution is found to lower the risk level.
Compliance
The second pillar of CASB is compliance. Organizations are often tasked with ensuring that their systems meet certain data privacy and security regulations, such as PCI DSS, PHI, HIPAA, and others, depending on the organization’s location, and the type of sensitive data they are using and storing. Despite not being stored on-premises, data and applications on the cloud must also meet these regulations, and it is an organization’s responsibility to ensure regulatory compliance extends to data in the cloud.
Sometimes, the visibility provided by CASB solutions is enough to ensure regulatory compliance. When this isn’t enough, CASB can also be used to create detailed security policies which are designed to meet specific regulatory requirements especially for cloud-based data storage and applications.
In addition, good CASB solutions can facilitate identification of enterprise security issues that may risk an organization’s regulatory compliance, so that they can be fixed, enabling the organization to avoid penalties associated with non-compliance.
Data Security
The third CASB pillar is data security. The more an organization’s data is distributed across different locations and platforms, the harder it is to control and maintain data security. Organizations choosing to use applications in the cloud need a way to ensure that all data flows, both in and out of the cloud, remain secure at all times, despite their diverse destinations.
Many traditional enterprise data security systems were designed to protect only data that is stored on-premises. Most solutions that also offer support for protection of data in the cloud were not developed for that purpose, and fall short in some areas. For example, a traditional data-loss prevention system (DLP) won’t proactively protect the data stored in the cloud in the way that cloud access security brokers do. Relying just on traditional DLP increases the risk of data loss. However, combining both solutions, DLP and CASB, will cover all gaps between an organization and the cloud, for maximum data security.
Threat Protection
CASB issues detailed alerts when suspicious user behavior is detected on an organization’s systems, such as when someone attempts to gain access to a cloud app from an unknown device, or from an unusual location, or if someone tries to download or access sensitive data in an unusual manner. For example, if a user suddenly tries to download a lot of data at once, the CASB will block the attempt and ‘raise an alarm’ regarding the unusual behavior. In this way, the CASB can identify malicious threats inside the organization, and also block hackers who may have already gained access to the cloud using stolen user credentials, DDoS attacks or through other means.
The most advanced CASB solutions often use machine learning technology and behavior analytics, including accumulated information about expected patterns of cloud usage, to allow for accurate identification of suspicious user behavior. This enables maximum access control and high standards of enterprise security.
The role of CASB against shadow IT
One of the use cases for CASB is for effective protection against common Shadow IT practices. Shadow IT refers to situations in which an end-user accesses an unauthorized application, including cloud services, without explicit approval from the organization’s IT department. Often, Shadow IT is used by legitimate and dedicated employees to increase productivity and efficiency. Applications commonly used for Shadow IT include Dropbox for file sharing and Skype for meetings, as well as Google Docs and Microsoft Office 365 for creating and sharing documents. Sometimes, these are used to bypass strict security protocols that are seen by employees as slowing down or disrupting their workflow. However, despite an employee’s best intentions to work more efficiently, unapproved access presents a significant security risk, as other parties could gain access to sensitive data that is shared across multiple applications, or from devices outside the organizational network, such as an employee’s phone or home computer. As bring-your-own-device (BYOD) becomes more popular at the workplace, this risk increases. The access control functionality provided by CASB can decrease this risk, by identifying and blocking any user attempts to access and use unauthorized applications in the cloud.
CASB modes
Cloud access security brokers may use one or more of the following deployment modes:
API mode
CASB solutions that use API modes are asynchronous, ‘out-of-band’ solutions. When data is sent to the cloud, it triggers an API call, activating the CASB. The CASB can then analyze cloud usage, and enforce policies as needed. As the CASB is outside of the network, it has little to no effect on network performance, so it doesn’t affect user productivity. This mode also provides thorough coverage for all data sent to the cloud, including from both managed and unmanaged devices. It also works for user-to-cloud and cloud-to-cloud traffic. This is especially relevant for organizations working with many cloud services and cloud service providers. API-based CASBs allow the application of new security policies to both new cloud traffic and existing data (‘data-at-rest’). However, there is a downside – during the delay between data being sent and it arriving at the CASB, the data is left unprotected. In addition, not every cloud provider will support an API-based CASB solution.
Forward proxy or reverse proxy mode
Using a proxy mode, the CASB sits between the enterprise network and the cloud applications being accessed. Acting like a gate, it monitors and enforces enterprise security policies in real time, providing visibility and control over current cloud usage. In forward proxy mode, a CASB agent must be installed on every user device – this is known as ‘first mile’ technology. This means that it doesn’t work for unmanaged devices. In reverse proxy mode, however, the CASB sits directly in front of the cloud services being used. This is ‘last mile’ technology, and is suitable for managed and unmanaged devices. In either proxy-based mode, protection occurs in real-time, leaving no time during which the data is unprotected. Unfortunately, network performance may be negatively affected by this real-time threat protection solution.
Log collection mode
In log collection mode, the CASB processes log information from other enterprise security infrastructure, such as firewalls. This provides more limited information than other modes, usually restricted to monitoring activity, without the ability to analyze the actual data content. It can provide insight into user behavior that can then be used to control access to the cloud.
Choosing a CASB vendor
When it’s time to choose the right CASB solution for your organization, there are a number of cloud security capabilities to look for. The following checklist, based on Gartner recommendations, summarizes capabilities mentioned above:
- Identification of cloud applications currently in use
- Risk level assignment for existing cloud services
- Granular policy creation for cloud usage
- Enterprise security policy enforcement
- Corporate data loss prevention
- Detection of malicious threats from outside the network
- Insider threat detection
- Cloud access control provision
- Ongoing cloud usage monitoring
- Behavior analytics and machine learning technology for unusual behavior detection
- Log collection and management
- Compatibility with different deployments
- Coverage for managed and unmanaged devices