EvilProxy Broadens AitM Cyberthreat with Phishing-as-a-Service Tool
by Peter Fell
Posted on March 28, 2023

Think your logins are secure because you’ve implemented multi-factor authentication (MFA)?
Think again. EvilProxy is a new and alarming cyberthreat that makes it easy for cybercriminals with limited technical expertise to launch reverse proxy phishing attacks that can steal authentication tokens and bypass MFA. And it’s available on the dark web for the bargain basement price of just $150.
We’ve written before about Adversary-in-the-Middle (AitM) attacks and how hackers use reverse proxies that steal session cookies, which they use to bypass MFA. But AitM-as-a-service is a dangerous new twist that is set to popularize – among cybercriminals, that is – a technique that until now, only technologically savvy hackers could deploy.
Stolen Cookies
Cookie Monster is not the only one saying “Me want cookie!” these days. Cybercriminals want your cookies – at least specific ones – since with them, they can defeat multi-factor authentication protections that would otherwise prevent them from gaining access to high-value accounts.
An AitM attack starts with hackers using a phishing campaign to convince users to login to one of their accounts, with a link that’s routed through a reverse proxy. The website that’s reached looks like the real thing – only in truth, it’s a site belonging to the attacker. When the user enters login credentials, they are passed on from the spoofed site to the real one, which issues an authentication factor to the user.
Once the user has authenticated with that factor, the site MFA passes a session cookie that authenticates the user back to the user’s browser. Except in this case, the AitM intercepts the cookies along the way. The cybercriminal now has the user’s login credentials as well as a session cookie that allows them to bypass MFA and freely access the account until the cookie expires. And since the user is now logged on to their desired application, it is likely that they are not even aware of what just happened.
Phishing-as-a-Service
Corporations aren’t the only entities increasingly reliant on cloud-based SaaS solutions. Cybercriminals have also discovered the convenience of cloud-based tools.
Phishing-as-a-Service has been a favored tool of advanced persistent threat (APT) actors for some time. Why bother to build your own custom software to launch cyberattacks – or be limited by your inability to do so – when for a modest fee you can purchase the capability on the dark web?
Muraena/Necrobrowser, Modlishka, and Evilginx2 are just a few examples. Another one that Microsoft has been tracking is known as DEV-1101. DEV-1101 came onto the scene in May of 2022. The kit is open source with a $100/month licensing fee. It provides ready-to-go phishing pages that are convincing replicas of widely used tools such as Microsoft Office. It includes a variety of advanced capabilities including detection evasion and management through Telegram bots.
EvilProxy
EvilProxy is a new addition to the Phishing-as-a-Service scene. What makes this AitM tool different is that the previously mentioned kits require some technical sophistication to deploy. The creators of EvilProxy seem obsessed with customer service and being user friendly – wonderful qualities, except for the fact that it is criminals they are serving. The software is simple to deploy, has an easy-to-use graphical interface, and comes complete with online tutorials and instructional videos.
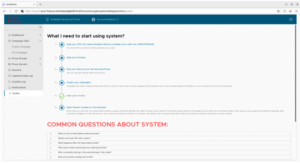
Dark web monitoring company Resecurity captured this screenshot from EvilProxy. Some legitimate software companies could learn a thing or two from this interface:
EvilProxy comes complete with ready-to-deploy pages for many leading services that cybercriminals might want to hack into.
EvilProxy makes it simple for common criminals who want to get in on the action of the fast-growing cybercrime business to do so, without having to spend years building up their programming skills. A sharp increase in phishing-based AitM attacks is sure to result from the availability of this easy-to-use service.
Protecting Against Credential Theft
Detection-based blocking of dangerous sites, like the spoofed ones used in AitM attacks, is like using a mesh umbrella to keep out the rain. Zero-day exploits pass right through, since. they’re so new that detection-based solutions haven’t yet discovered them, or their signatures haven’t yet reached the endpoints, where they should be blocked. In fact, phishing success is largely a result of threat actors acting promptly to take down their sites long before detection-based solutions catch up.
User training helps but can’t be relied on. Many social engineering approaches employed for phishing are brilliantly designed to bypass the red flags highlighted in training. What can be relied on is that at some point, busy and distracted users who receive dozens of emails each day will mistake a phishing email for one that’s legit and click when they shouldn’t. Many studies have shown that even sophisticated and trained users fall for phishing attacks a distressingly high percentage of the time.
It takes an integrated Zero Trust Secure Service Edge (SSE) solution to stop these sophisticated phishing attacks. ZTEdge Web Isolation opens email links in a virtual browser that is isolated in the cloud, where malware can do no harm. While the safe rendering content sent to the endpoint browser generally allows full interactivity, the ZTEdge SWG can be configured to open unverified or unknown sites in full “read only” or “prevent login” modes to keep users from entering credentials – and thereby stop the AitM process before it gets started.
Web Isolation and our isolation-backed SWG are just two elements of the full-stack, cloud-delivered ZTEdge SSE platform, designed to secure work that gets done via user browsers – that is, on SaaS and webapps as well as general web and emails use – both in the office and remotely, on managed and unmanaged devices. ZTEdge delivers comprehensive state of the art cybersecurity via the Ericom Global Cloud Platform, in a way that it is easy to deploy and won’t break our customers’ budget.
About Peter Fell
Peter Fell, Group CTO - EME, is a solutions architect and information security expert, specializing in data protection, cybersecurity, data privacy and compliance. He has 20+ years experience in Information Security, specializing in Data Protection, Cybersecurity, Data Privacy and Compliance, SaaS, Identity and Access Management.Recent Posts

Air Gapping Your Way to Cyber Safety
Physically air gapping enterprise networks from the web is a great way to protect operations, keep data safe … and squelch productivity. Virtual air gapping is a better approach.

Motion Picture Association Updates Cybersecurity Best Practices
The MPA recently revised its content security best practices to address, among other challenges, the issue of data protection in the cloud computing age.

FTC Issues Cybersecurity Warning for QR Codes
QR codes on ads are a simple way to grab potential customers before they move on. No wonder cybercriminals are using QR codes, too.